Message Authentication Code MAC Definition and Use in EFTs
Message Authentication Code (MAC): Definition and Use in EFTs
A message authentication code (MAC) is a security code typed in by a computer user to access accounts or portals. This code is attached to the message or request sent by the user. MACs must be recognized by the receiving system to grant access.
Key Takeaways
– MACs are a security measure attached to electronic financial transactions.
– Codes are randomly generated by algorithms.
– MACs ensure that messages can be sent only once.
– In the communications industry, MAC also stands for media access control, so the term message integrity code (MIC) is used instead.
Understanding Message Authentication Codes (MACs)
MACs are commonly used in electronic funds transfers (EFTs) to maintain information integrity. They confirm that a message is authentic, comes from the stated sender, and hasn’t changed en route. A verifier with the key can identify changes to the message’s content.
Note
MACs are required to access any financial account. Banks, brokerage firms, trust companies, and any other deposit, investment, or insurance company that offers online access can employ these codes. They are a vital component of financial cryptography.
Algorithms Used to Generate MACs
Three algorithms typically comprise a MAC: a key generation algorithm, a signing algorithm, and a verifying algorithm. The key generation algorithm chooses a random key. The signing algorithm sends a tag when given the key and message. The verifying algorithm verifies the authenticity of the message when given the key and tag; it will return a message of accepted if the message and tag are authentic and unaltered, but otherwise, it will return a message of rejected.
The message should contain data that ensures it can be sent only once. For example, a one-time MAC, timestamp, or sequence number could guarantee that the message is sent only once. Otherwise, the system could be vulnerable to a replay attack, where an attacker intercepts the message, decodes it, and retransmits it later, replicating the original results and infiltrating the system.
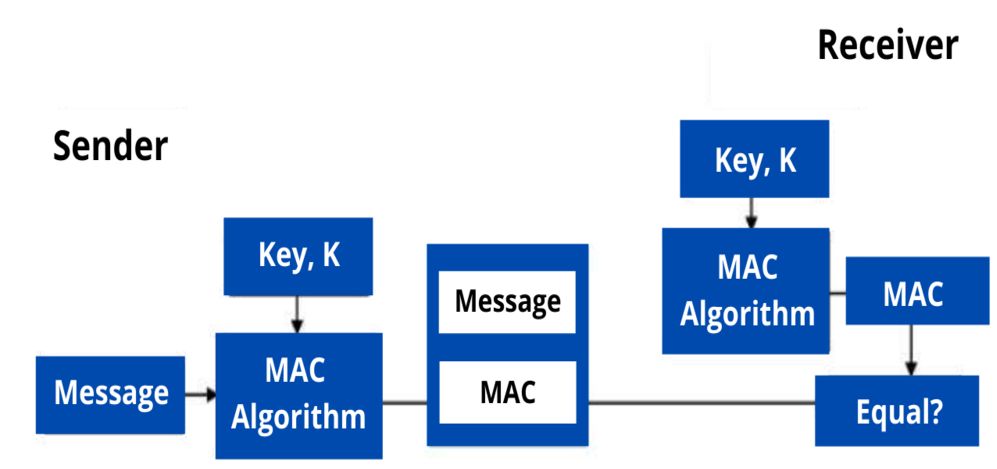
For example, the sender sends a message, such as an EFT, through the MAC algorithm, which generates a key and attaches a MAC data tag to the message. The recipient gets the message, runs it back through the MAC algorithm with the same key, and gets a second data tag. They will then compare this MAC data tag with the first one attached to the message when it was transmitted. If the code is the same at both ends, the recipient can safely assume that the message’s data integrity is intact. If not, it means that the message was altered, tampered with, or forged.
Message Integrity Codes (MICs)
Sometimes, the term message integrity code (MIC) is used instead of MAC. This is most often done in the communications industry, where MAC traditionally means media access control address (MAC address). However, MIC can also refer to message digest, which does not use secret keys in the same manner as a MAC and cannot offer the same level of security without further encryption.
Frequently Asked Questions
– What Is the Difference Between a Message Authentication Code (MAC) and a Digital Signature?
With MACs, the same key is used by both sides of a message—the sender and the recipient. This is so the recipient can verify the message has not been altered or otherwise interfered with en route. A digital signature serves only as verification that a message was sent by the owner of the digital signature.
– What Is the Alternate Name for a Message Authentication Code (MAC)?
MACs are commonly called tags. They are a type of cryptographic checksum and may be referred to as such. Cryptographic checksums use cryptographic algorithms to assign matching data to both ends of a message for verification purposes.
– What Is a Message Authentication Code (MAC) Used For?
MACs can be used anytime it is necessary to ensure that a message has not been altered or tampered with in transit to the recipient. They are commonly used for electronic funds transfers (EFTs), but they are not unique to that type of transaction.
The Bottom Line
Message authentication codes (MACs) are a common way to ensure the integrity of a message and are useful for EFTs. The codes are randomly generated by an algorithm. Financial institutions that allow transfers of funds typically use MACs as part of their security.