Understanding Double-Spending and How to Prevent Attacks
Double-spending is the risk of cryptocurrency being used multiple times. Modified blocks can be added to the blockchain, allowing the initiator to reclaim spent coins.
Key Takeaways:
– Double-spending occurs when someone alters a blockchain network to reacquire a cryptocurrency.
– Double-spending is less likely than theft from an inadequately secured wallet.
– Attacks such as the 51% attack and unconfirmed transaction attack are commonly used for double-spending.
To understand double-spending, it is helpful to understand how the blockchain works. Each block contains a timestamp, information from the previous block, and transaction data, which is encrypted using a security protocol.
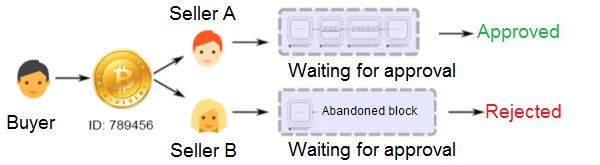
To double spend, a secret block must be mined faster than the real blockchain. This chain must be introduced to the network before it catches up. The perpetrator can then use the spent cryptocurrency again.
Double spending is minimized by the blockchain, as the likelihood of accepted altered blocks is very slim. Even if a modified block is accepted, it would be outdated and rejected by the network. No recorded instance of double-spending exists, but the same attacks can be used for other purposes.
Double-spending attacks are most significant in the form of the 51% attack, where a miner controls a majority of the hashing power. Forked cryptocurrencies with smaller networks are vulnerable to this attack. The unconfirmed transaction attack also fools users.
Although there have been attempts, double-spending is uncommon. The blockchain and consensus mechanism do not accept copied bitcoins.
Several variations of attacks can enable double-spending, including the Finney attack, race attack, and unconfirmed transaction attacks.